
by MIke Kell | Aug 1, 2025 | Cybersecurity, Cybersecurity Consulting, Unified Network
The CMMC OMB Review marks the final stage before the Cybersecurity Maturity Model Certification (CMMC) rule is finalized. For small and medium DIB contractors, this is the time to complete your Level 1 SPRS self‑assessment and secure DoD contract eligibility. Here’s...

by MIke Kell | Dec 16, 2024 | Cybersecurity, Cybersecurity Consulting, Governace, Leadership
Governance, Risk, and Compliance (GRC) frameworks empower organizations to manage cyber risks effectively, and as a board member, you have a pivotal role in steering these efforts. This guide provides a practical roadmap to help you oversee cybersecurity strategies,...
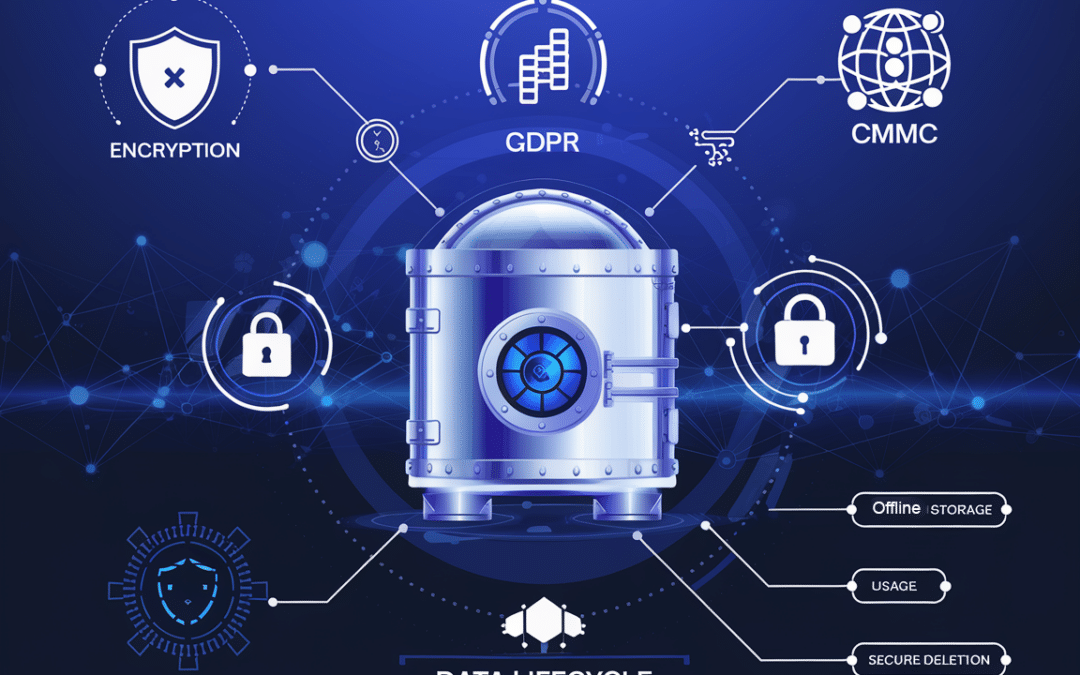
by MIke Kell | Dec 9, 2024 | Cybersecurity, Cybersecurity Consulting
Let’s talk about why data protection and privacy are critical for the success and resilience of the organizations you oversee. You’ve probably heard the phrase “data is the new oil”—and it’s true. Data drives business decisions, innovation, and competitiveness. But...
by MIke Kell | Dec 3, 2024 | Cybersecurity, Cybersecurity Consulting
Why Network Security Should Be a Boardroom Topic Executives must view network security as a strategic priority that underpins trust with clients, investors, and employees. This guide explores how foundational network security practices can be integrated into modern...
by MIke Kell | Nov 22, 2024 | Cybersecurity, Cybersecurity Consulting, Governace, Leadership
Building a Cyber-Resilient Organization: Where Strategy Meets Security Let’s face it—cybersecurity is no longer just a technical responsibility. In today’s digital-first world, it’s a business-critical priority. Every headline about data breaches serves as a stark...
by MIke Kell | Oct 29, 2024 | Cybersecurity Consulting, Leadership
Executives need to understand the basic concepts of networking and cybersecurity to grow their businesses. In today’s technology landscape, buzzwords like “Zero Trust” and “Artificial Intelligence” dominate discussions, often presented as...







